Registration to HackWithInfy is open through InfyTQ, the Infosys learning and engagement platform for engineering students in India. Students who are already registered on InfyTQ can apply for HackWithInfy by clicking on the HackWithInfy program banner on the InfyTQ website homepage. Students who have not joined InfyTQ, can visit the InfyTQ website to create an account and register for HackWithInfy.
- The mode option only affects the newly created file.
- Here’s how you can uninstall applications known to cause this Blue Screen error.
- Involved departments can include administration, marketing, production, and employee training.
Restoring a backup is faster than re-installing the OS and applications. Expect to get massive virus infections regardless of how often you clean your computer or run antivirus programs. You are inviting the most dangerous of the bad into your computer. The insurance industry reportedly is trying to figure out how to clearly include or exclude coverage for cyber risks, or even figure out how to address the issue. Viruses used 0x80070643 to be the most common type of harmful program that users encountered in the 1990s; today, most people are more likely to encountertrojans,wormsor other types of threats. Adhering to these steps won’t necessarily protect your computer system from every virus, but you’ll significantly minimize threats from viruses. Businesses in particular often encounter security hazards online, since some cyber criminals target merchants.
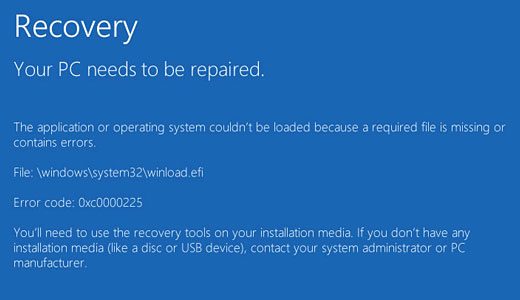
Part 1 What Is A File System Error?
Deleting Win dump files depends on the type you are working with The call for deleting win dump files comes majorly because of Memory.dmp files. This is because they take up a large space on the system, especially when running large applications when the error occurs. Banner error messages display at the top of the page, when SEVIS finds one or more errors on a page. These validation errors must be corrected before the user can continue. To address these errors, correct the bulleted information listed in the error message. Knock on wood, this has not happened to me in a very, very long time, but every once in a while the Microsoft Windows system files will become corrupted and report errors.
All-in-one data recovery software to recover files, media, or entire partitions. I have run sfc /scannow several times and it verifies 100% and reports that files were found to be corrupt and repaired. I could Reset Windows as you suggest but although it will keep my files it would remove my programs.
Post jobs, collect applications, schedule and conduct interviews, and monitor candidates with applicant tracking. Get new hires up to speed with our onboarding system. And potentially save thousands in tax credits with Work Opportunity Tax Credit screening. Heartland offers a wide range of reporting capabilities to help you manage your payroll taxes and stay compliant.
How To Find Latest Windows 10 Version Number?
When setting the priority for an HTTP/2 stream, the stream may be marked as a dependency for a parent stream. This error code is used when an attempt is made to mark a stream and dependent of itself. Indicates that an attempt is being made to access a variable that is not defined.
To find it, type “Windows Security” in your PC’s search bar. Click the shield icon on the left to see your latest scan. As with other viruses and worms, Klez was released in several variants. It infected files, copied itself, and spread throughout each victim’s network. It hung around for years, with each version more destructive than the last. Some viruses disable System Restore and other important Windows tools such as Task Manager and CMD.